“A man is crazy who writes a secret unless he conceals it from the crowd,” wrote 13th-century philosopher Roger Bacon. Since ancient times, politicians, military leaders and even lovers have used ciphers to encrypt confidential messages. “The purpose of using codes and ciphers has largely remained the same over the centuries,” says Mark Frary, author of The Story of Codes: “to communicate messages in such a way that enemies cannot read them.”
“Messengers in Ancient Greece had messages tattooed on their shaved heads before their hair grew back. A slow method, but with the same intention as messages encrypted using Germany’s infamous Enigma machines,” Frary says. “Businessmen using the telegraph in its early days often used codes to hide details of pricing and orders. Today, financial transactions over the internet are kept secret using encryption.” Historical figures from Julius Caesar to Thomas Jefferson used ciphers, and some systems—like the Masonic Cipher—have been in use for hundreds of years. Here are eight legendary ciphers that changed the world.
1. Scytale

The Spartans had a relatively simple but effective way of sending encrypted messages over long distances: The scytale, a wooden rod that could be wound with parchment strips on which a message was written. When unwound, the message was non-legible. When wound back onto a scytale of the same circumference, the message would be revealed.
Plutarch, writing in the first century, described how the Spartans used the scytale:
“They make two round pieces of wood exactly alike in length and thickness, so that each corresponds to the other in its dimensions, and keep one themselves, while they give the other to their envoy…Whenever, then, they wish to send some secret and important message, they make a scroll of parchment long and narrow, like a leather strap, and wind it round their scytale…. he reads around the staff, and so discovers the continuity of the message.”
Once the circumference of the scytale was known, the code was easily broken, and the method was only useful for transcribing shorter messages.
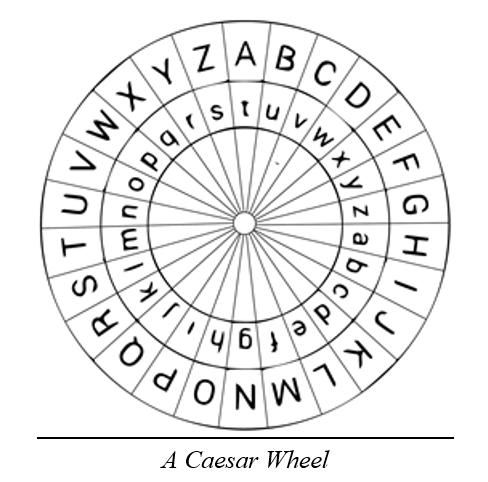
2. Caesar Cipher
Caesar Ciphers involve shifting each letter of a message by a set number of letters. Roman General Gaius Julius Caesar used this substitution method in correspondence with friends back in Rome while he was campaigning in Gaul. Roman writer Suetonius says that Caesar “changed the order of letters in such a way that no word could be made out. If somebody wanted to decipher it… he had to insert the fourth letter of the alphabet, that is D for A, and so on.”
Caesar was so fond of using various encryption methods in his correspondence that Valerius Probus wrote an entire treatise on Caesar’s techniques in the year A.D. 1 (a text that is now lost to history). What survives is Caesar’s own account of the Gallic wars in which he describes sending a besieged Cicero a letter in Greek instead of Latin “lest the letter being intercepted, our measures should be discovered by the enemy.” For good measure, the letter was attached to a spear and hurled into Cicero’s camp, where it was lodged in a tower for two days before being discovered.
Did you know? The Kama Sutra, written in the 4th century, recommends young ladies learn the art of secret writing to arrange trysts.
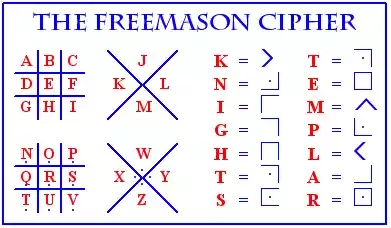
3. Freemason Cipher/Pigpen Cipher
Freemasons of the 18th century used the Pigpen Cipher to encrypt messages. Rather than switch out letters, it placed letters on a grid and used the adjoining angles made by the grid’s lines, paired with a series of dots, to represent the letter contained within it. It’s also known as the Masonic Cipher, Napoleon Cipher, and Tic-Tac-Toe Cipher.
“Its first usage has been long forgotten but some say it was first used by rabbis to encode messages in Hebrew,” says Frary. Pigpen ciphers were mentioned as early as 1531 by German polymath Heinrich Cornelius Agrippa in his Three Books Concerning Occult Philosophy, and they continued to be used for centuries. “They were being used by the British in the American War of Independence,” says Frary. “Pigpen ciphers became more commonplace in the 18th century when they were used by Freemasons, so much so that it became called the Freemason Cipher,” Frary says.
4. Great Cipher of Louis XIV
Created by the father-son duo of Antoine and Bonaventure Rossignol, the Great Cipher was used by Louis XIV to transmit sensitive political messages and remained unbroken for 200 years. While previous ciphers used 26 symbols (the number of letters in the alphabet), the Great Cipher used 587 numbers to represent French syllables instead of single letters, and further complicated matters by making some numbers indicate deletions. One of the Sun King’s more interesting messages decoded by cryptanalyst Étienne Bazeries contained the possible identity of the Man in the Iron Mask.
Did you know? A cracked cipher was a death sentence for Mary, Queen of Scots. A double agent smuggled encrypted letters to and from the imprisoned Mary to seek her approval of a plot to assassinate her rival and captor, Queen Elizabeth. The letters were delivered to and decoded by Thomas Phelippes, England’s foremost codebreaker.
5. The Jefferson Wheel Cipher
Founding Fathers like Thomas Jefferson, James Madison, John Adams, and James Monroe all used ciphers to encrypt their correspondence during the American Revolution. Jefferson even invented several ciphers of his own.
Jefferson was inspired to create the Jefferson Wheel Cipher while serving as American Ambassador to France. Since the Renaissance, European courts had employed “black chambers” of cryptanalysts who intercepted sensitive mail from the post office, copied and decoded it, then sent it back on its way. To get around them, Jefferson created a wooden object that resembled a rolling pin covered in letters. The cipher was comprised of 36 wooden discs on a metal axle, with the letters of the alphabet set in random places on each wheel. The sender would write a normal sentence in one horizontal line, and while the wheels were all in that position, copy down a nonsense band of horizontal letters in another line, then send only the nonsense string of letters to the recipient. When the recipient recreated that string of letters on their cipher, they would also recreate the actual, legible message.
In 1802, then-President Jefferson sent a cipher to U.S. Ambassador to France Robert R. Livingston, writing: “I send you a cipher to be used between us, which will give you some trouble to understand, but, once understood, is the easiest to use.” Jefferson also sent Merriweather Lewis a square table cipher in 1803 to use on his expedition with William Clark to explore land for the Louisiana Purchase.
6. Morse Code

The invention of the telegraph in the early 19th century permitted messages to be sent over long distances at great speed. American inventor Samuel Morse patented a binary system called Morse Code where dots and dashes replaced numbers and letters. Telegraph clerks translated messages for clients into Morse Code and sent them out over telegraph wires to stations where they would be re-converted into text. There was one major drawback. As a writer in the English Quarterly Review highlighted in 1853: “Means should also be undertaken to obviate one great objection, at present felt with respect to sending private communications by telegraph—the violation of all secrecy—for in any case half-a-dozen people must be cognizant of every word addressed by one person to another.”
Did you know? The Voyager Golden Record included “Per aspera ad astra” (“through hardships to the stars”) in Morse code.
The telegraph’s privacy issue led to a resurgence in interest in ciphers and the reemergence of old ones. “Morse code was frequently combined with other encryption methods,” says Frary. “The message was first encrypted using one method and then converted into Morse code for transmission.” For example, the American military adapted the 15th century Vigenère cipher to create cipher disks of their own when relaying sensitive information.
SUPER RARE WWII Code Breaking Machine
7. The Enigma Code

The Enigma Machine looks more like a typewriter than a weapon, yet it was one of the most powerful tools in the German military arsenal during World War II. Invented in 1918 by Arthur Scherbius to encrypt business information, it became infamous during the second world war as the preferred way for the Nazis to send confidential communications. It was portable, fast, and largely automated. Typed text was automatically encrypted by the machine, then transmitted by radio. The receiver would type the coded message into their Enigma machine and the machine would automatically produce the decoded message.
It was also highly secure: The Enigma Machine had a series of scrambler disks with 26 letters of the alphabet (by 1938, each machine had five scrambler disks). The German military produced daycode books so machines on the sending and receiving ends were tuned to the same settings, which were then changed every 24 hours. That meant each message intercepted by the Allies had over 150 million million million possible combinations to explore.
“Breaking it manually was almost impossible, although Polish codebreakers, incredibly, did manage to do just that,” says Frary. “As the Enigma machines became more complicated, the codebreakers at Bletchley Park in the UK were forced to develop, in the first instance, mechanical bombes [a mechanical device developed by mathematician Alan Turing] to help with the decryption and then one of the first computers, the Colossus.”
By war’s end, over 2.5 million messages had been decoded. To avoid revealing that they’d cracked the Enigma Code, the British invented an MI6 spy named “Boniface” who was the alleged source of the intercepted information.
Navajo Code Talkers: Zonnie Gorman
When the Marine Corps sought to create an unbreakable code during World War II, they decided to base it on a complex, unwritten language that was relatively unknown outside of a small population: Navajo. The 29 members of the Navajo Nation they hired to create the code became known as “The Navajo Code Talkers,” and were involved in every Marine operation in the Pacific Theater. The code contributed to critical victories against the Japanese like the Battle of Iwo Jima.
“After the war, Japan’s chief of intelligence admitted they had broken the U.S. Air Force codes but had failed miserably with the Navajo code,” says Frary. The code remained unbroken during the war and the top secret program’s existence was only declassified in 1968.
The Navajo were not the first Native Americans to lend their language skills to America’s armed forces; during World War I; at least five different tribes including the Choctaw used their native languages to relay intelligence.